Sensible IPAM Part 5: Security of IP Infrastructure
Learn how to manage security for your scattered network environment. Security is key when it comes to avoiding DDos attacks and mitigating human errors, so here is what you can do to stay ahead.
Jul 19th, 2022
For our final blog from our sensible IPAM series, we look deeper into how to manage security for your scattered network environment. Security is key when it comes to avoiding DDOS attacks and mitigating human errors, so here is what you can do to stay ahead.
Each part presents real-world problems for which Men&Mice has provided solutions.
It All Comes Down To Security
Imagine that you are:
- The CTO of a Managed Service Provider, whose own network is the first line of defense to protect customers. Your services are sensitive, as gaining access to or bringing down your network would compromise those utilizing your MSP solution.
- The Lead Network Administrator of a mid-sized enterprise company recently expanding with new employees (and devices), through M&A activities, arriving daily. Onboarding new people is your technological challenge, balancing their need for autonomy and network resources with your requirement to maintain security protocols.
These problems emphasize the importance of security more than ever as they can potentially severely compromise your network.
What You Need
Much of network security is inherently present in the technology used. Orchestration and synchronization between different software providers, interfaces and hardware, however, needs to be done well.
Good security practices must be sensible to be ubiquitous across the network, instead of obstructive. They must be simple at their core and robust in their execution to prevent and solve problems. Networks are complicated enough.
Some of the more overlooked security vulnerabilities in network management today include:
- Visibility challenges, or lack of central, unified overviews resulting from incompatible or simply different services (the variety of interfaces and functionality of each individual service that comprises the entirety of a network)
- Misconfigurations or incompatibilities (what you do in one area of your network may not synchronize or be compatible with another area of the network, particularly with cloud vendors).
- Human error (automation can remove this ever-present challenge, increasing the health of the network).
- Loss of control (how can you restrict access to increase security and focus on providing autonomy only where needed.)
Where Micetro Can Help
Retaining network security on the DNS, DHCP and IP address level has been a core design principle for Micetro from day one (which was over 30 years ago). Managing the fundamental components of the network means great responsibility: if the foundations are compromised or out of sync, the entire network is at risk.
The first security risk Micetro has addressed in the evolving world of hybrid network management, was to eliminate synchronization and misconfiguration hurdles between on-prem services and cloud services, then across cloud providers, enabling greater automation and utilization of network resources, independent of what are the services themselves. Then, we centralized management of these diverse and otherwise incompatible resources into one place.
This backend-agnostic, API-first overlay approach gave way to the xDNS Redundancy feature, which helps further mitigate DDoS and other malicious attacks.
If parts of the network become unavailable during an event like a DDoS attack, xDNS Redundancy prevents shutdown by switching to alternate resources. Once the affected resources are once again accessible, changes and updates are automatically synced across the entire network.
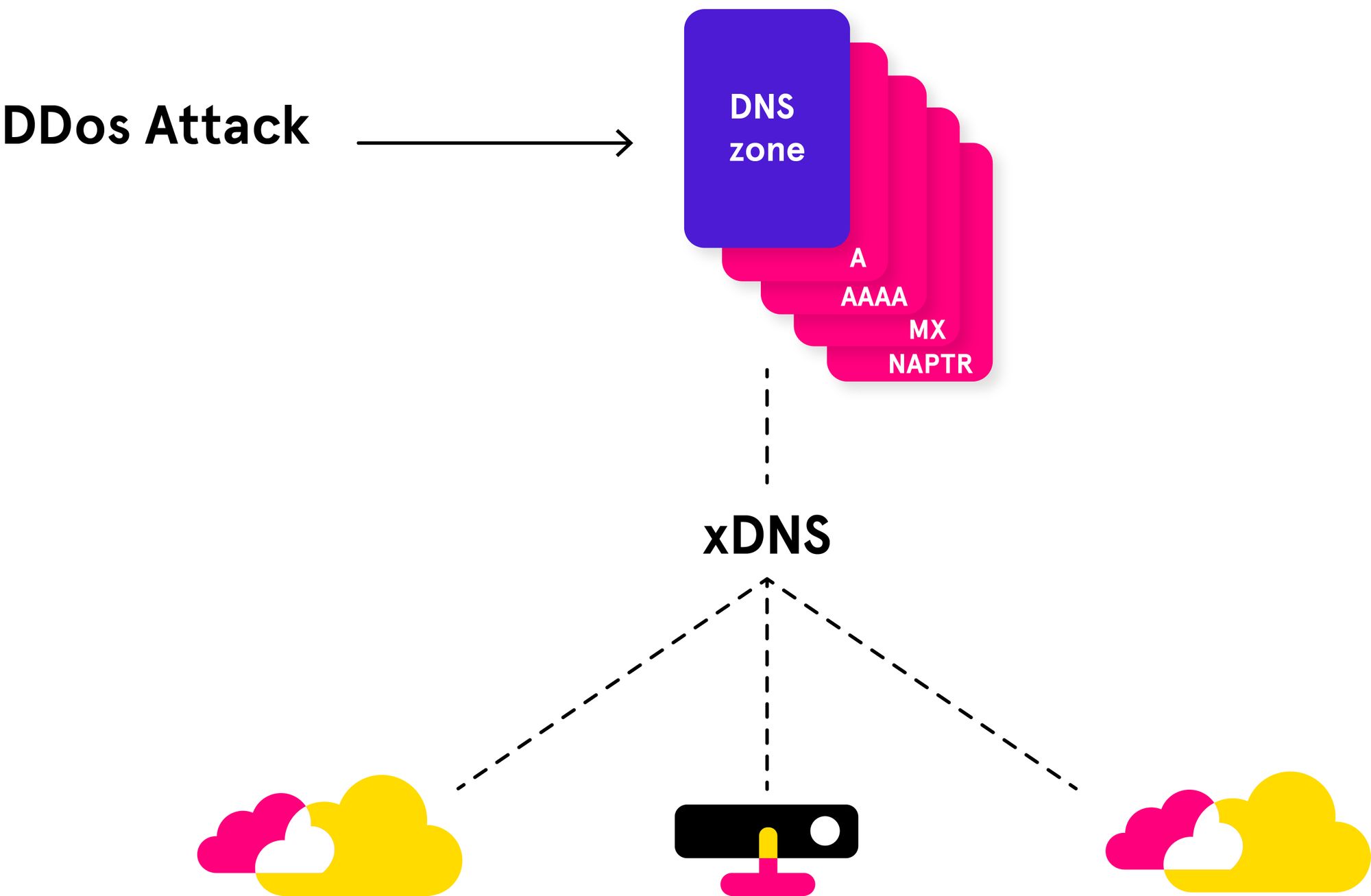
Due to Micetro’s powerful, compatible APIs, different network resources are processed and managed the same way within Micetro. This means that replicating or migrating DNS zones or DHCP scopes between network environments requires no special consideration or prolonged processes, making your DNS, DHCP and IPAM nimbler.
In addition, health alerts within Micetro provide the visibility necessary to proactively address misconfigurations, address space overlaps and malicious attacks while minimizing its effect on user experience.
Likewise, unified audit trails within Micetro help identify the source of an issue and on what area of the network, providing richer data to inform proactive decisions.
More often than any company would like to admit, especially in the age of post-Bring Your Own Device (BYOD) enterprise culture, security breaches can occur through human error. A simple password used across multiple mission-critical logins, a laptop stolen or left digitally unguarded, a malicious email attachment downloaded with malware, trojans or droppers, all can quickly take down or manipulate areas of your network, wreaking havoc.
Micetro’s granular access controls, including its integration with Microsoft Active Directory, provide solid security templates for preventing unnecessary access (and therefore unnecessary vulnerabilities) on the network. Retaining existing configurations and implementing new ones is easy, replicated, synched and scales as needed.
Reach Out
We'd love to hear your suggestions for what kind of IPAM related content you would like to see from us. Alternatively, if you're looking to get started with your IP address Management (IPAM), you can sign up for your free trial! The beauty of an overlay is that you can install it completely risk-free.